Landline:+86-0775-84649797 Phone:+86 19926651112(Same WeChat ID)
Share:
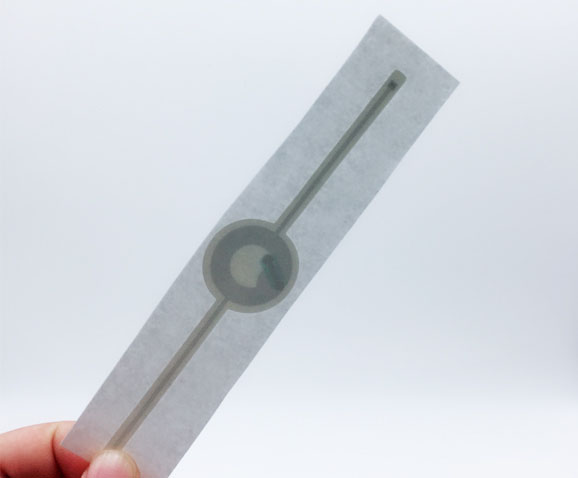
NFC & RFID Tags for Access Control
In the application of security protection, access control is the selective restriction of access to a place or other resource. The act of accessing may mean consuming, entering, or using. Radio frequency identification (RFID), especially those with near field communication (NFC) technology, often used in access control management. They provide security protocols that allow access only to people with clearance. These people might clear security by using an ID card or another device implanted with an RFID tag.
Whether you need to keep a gated community secure or track people at a large event, there are many RFID options for access control management. For example, a gated community might distribute RFID tags for residents to put in their cars. These tags allow them to clear the security gate and enter the community accordingly. Access control ensures that no one can enter a restricted area without physical authorization.

NFC Access Control Tags
Near field communication (NFC) technology is used for multiple applications, especially for protecting online security. This technology employs one NFC reader and one NFC card or key. The NFC key is normally coded with the tag data, which contains the data for authorizing the holder to access the designated room or area. That key is tapped over the NFC reader, which reads the data with the aid of NFC communication protocol sets, and grants access to the authorized person. This communication isn’t limited only to authenticating and granting access to the authorized person but records the access data, time, period of access, and many other parameters.
There are different types of readers that are used in access control; among those readers, an IP-based modern access control reader is a highly featured, secure and reliable access control device available in the market. This reader can easily be integrated into an IT network for achieving robust and secure access control with much additional security and operational features. A smart card is also being used in NFC-enabled devices, such as tablets, mobiles, and laptops to access cloud-based network and system resources over the internet. In this access control system, the smart card data is transmitted over the internet to the centralized location for granting of access into the entitled cloud computing resources.
The latest form of NFC access control system is being managed through the mobile applications installed on smart devices. Those mobile applications act as the key or a data tag for the NFC reader. When the mobile is swapped or tapped over the NFC reader, a communication channel is established over the air interface, and data transactions take place to authenticate the authority of the user to access the secured area, resources, or applications.

Access Control Management
In the world of access control management, an example might be a key card to an apartment complex. Residents swipe a key card embedded with an RFID tag. This tag is read via a radio signal by the card reader. The system checks the information against its backlog and returns it to the reader. If the tag is in the system, the door will unlock. These sorts of systems also are used in hotel key cards, high-security areas, and more.
There are so many kinds of RFID access systems. However, they all work based on this basic concept. This doesn’t mean there are no differences from system to system. Not every system is compatible with one another. For example, some systems use various levels of frequency. Access control systems often use low frequency (LF), high frequency (HF), and ultra-high frequency (UHF). LF is defined as being between 120 and 1355 kHz. HF is between 3 and 30 MHz. UHF, meanwhile, is between 300 MHz and 3 GHz.
Our Access Control Tags
Our RFID solutions for access control management come in the form of RFID wristbands, RFID cards, RFID tags, and RFID key fobs. This makes our tags ideal for every kind of access control system. Some RFID tags have waterproofing options for systems that are exposed to the elements. We also provide for tag printing, so you can label your tags as necessary. And these RFID tags can be programmed for specific functions to make it easier to put them in your system. They come in HF and LF frequencies, with some options for UHF, as well.
To learn more about this topic, please contact us.
Keywords:
Access Control / ID Card / RFID Card / NFC Access Control / RFID Access Control / Access Control Tags / RFID Tag / NFC Tag / RFID Auto Tags / RFID Car Tags / RFID Key Card / RFID Key Fob / NFC Key Fob / NFC Access Control Tags / Hotel key card / RFID Wristband
Inquiry